-
# gdb -n -q -x solmomth.py ./momsTouch import gdb import re key = [186, 28, 4, 248, 59, 168, 156, 124, 142, 152, 129, 137, 9, 85, 208, 238, 197, 253, 71, 80, 162, 70, 223, 99, 46, 81, 56, 254, 106, 242, 160, 90, 148, 229, 73, 98, 55, 31, 121, 216, 84, 28, 229, 104, 187, 240, 96, 100, 15, 73, 205, 125, 169, 253, 2, 125, 202, 3, 50, 128, 197, 75, 61, 233, 116, 141, 61, 138, 44, 178, 48, 120, 196, 0] flag = "0"*73 with open("input", "w") as f: f.write(flag) gdb.execute("break *0x8048812") gdb.execute("start < input") gdb.execute("set *0x8048819 = 0xb0469090") f = "" for i in range(73): ecx = int(re.findall("0x([0-9a-f]+)", gdb.execute("i r $ecx", to_string=True))[0], 16) print(ecx) f += chr((ecx^key[i])^ord("0")) gdb.execute("c") print(f)This problem can be solved by the brute forcing.

There is the checking ft.
And the next figure is the function's algorithm.
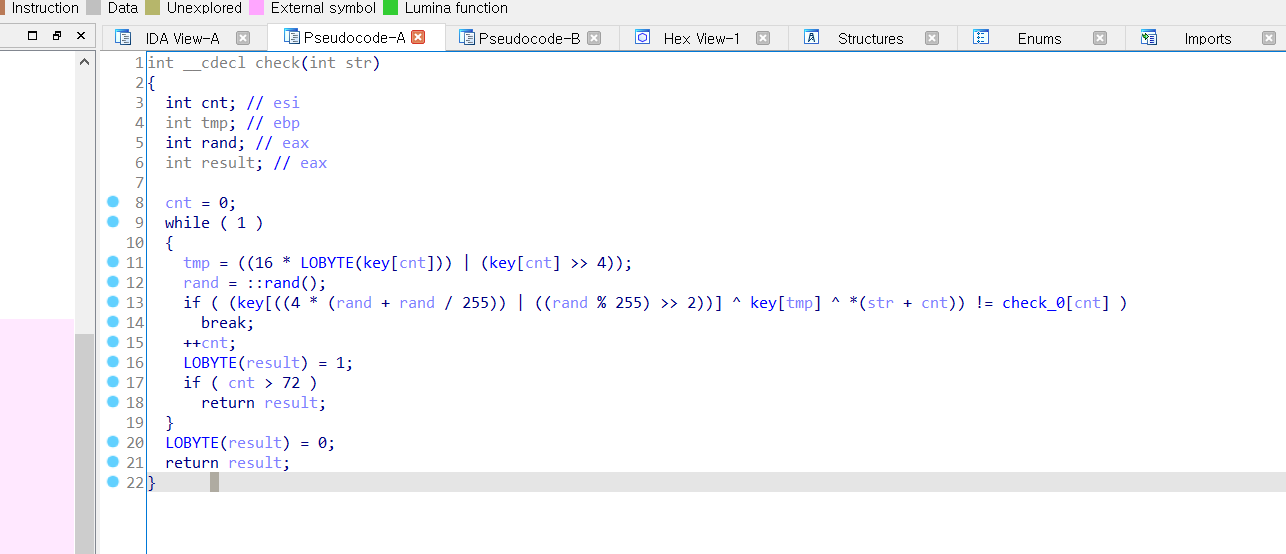
Since the checking algorithm use the xor, I just record the each value which is need to calculate correct input. Then, I did xor the original input to wrong output got the flag.
'Writeup > CTF_Writeup' 카테고리의 다른 글
[ ASIS CTF 2020 ] Latte (0) 2020.07.06 [ Defenit CTF 2020 ] Lord fool song remix (0) 2020.06.08 [ RCTF 2020 ] rust-flag (0) 2020.06.02 [ CODEGATE 2020 Preliminary ] RS(702pt) wripte-up (3) 2020.02.09 [Insomni'hack teaser] Kaboom writeup (0) 2020.01.21 댓글
ugonfor.
보안 위주로 가볍게 작성하였습니다 :)
